6.3 Cloud Security Threats (Fundamental Cloud Security U2C2) Cloud computing concept(chapter 6)
1.Traffic Eavesdropping
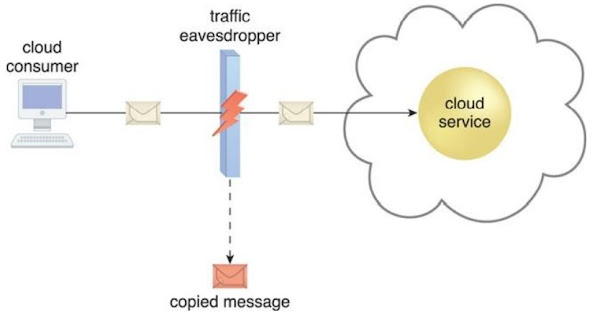
Traffic eavesdropping occurs when data being transferred to or within a cloud (usually from the cloud consumer to the cloud provider) is passively intercepted by a malicious service agent for illegitimate information gathering purposes (Figure 6.8).
The aim of this attack is to directly compromise the confidentiality of the data and, possibly, the confidentiality of the relationship between the cloud consumer and cloud provider. Because of the passive nature of the attack, it can more easily go undetected for extended periods of time.
Figure 6.8. An externally positioned malicious service agent carries out a traffic eavesdropping attack by intercepting a message sent by the cloud service consumer to the cloud service.
The service agent makes an unauthorized copy of the message before it is sent along its original path to the cloud service.
2.Malicious Intermediary
The malicious intermediary threat arises when messages are intercepted and altered by a malicious service agent, thereby potentially compromising the message’s confidentiality and/or integrity.
It may also insert harmful data into the message before forwarding it to its destination.
Figure 6.9. The malicious service agent intercepts and modifies a message sent by a cloud service consumer to a cloud service (not shown) being hosted on a virtual server. Because harmful data is packaged into the message, the virtual server is compromised.
3.Denial of Service
The objective of the denial of service (DoS) attack is to overload IT resources to the point where they cannot function properly.
This form of attack is commonly launched in one of the following ways:
• The workload on cloud services is artificially increased with imitation messages or repeated communication requests.
• The network is overloaded with traffic to reduce its responsiveness and cripple its performance.
• Multiple cloud service requests are sent, each of which is designed to consume excessive memory and processing resources.
Successful DoS attacks produce server degradation and/or failure, as illustrated in Figure 6.10.
Figure 6.10. Cloud Service Consumer A sends multiple messages to a cloud service (not shown) hosted on Virtual Server A.
This overloads the capacity of the underlying physical server, which causes outages with Virtual Servers A andB.
As a result, legitimate cloud service consumers, such as Cloud Service Consumer B, become unable to communicate with any cloud services hosted on Virtual Servers A and B.
The insufficient authorization attack occurs when access is granted to an attacker erroneously or too broadly, resulting in the attacker getting access to IT resources that are normally protected.
This is often a result of the attacker gaining direct access to IT resources that were implemented under the assumption that they would only be accessed by trusted consumer programs(Figure 6.11).
Figure 6.11. Cloud Service Consumer A gains access to a database that was implemented under the assumption that it would only be accessed through a Web service with a published service contract (as per Cloud Service Consumer B).
Within cloud environments, these types of attacks can lead to significant impacts depending on the range of IT resources and the range of access to those IT resources the attacker gains (Figure 6.12).
Figure 6.12. An attacker has cracked a weak password used by Cloud Service Consumer A.
As a result, a malicious cloud service consumer (owned by the attacker) is designed to pose as Cloud Service Consumer A in order to gain access to the cloud-based virtual server.
Virtualization provides multiple cloud consumers with access to IT resources that share underlying hardware but are logically isolated from each other.
Because cloud providers grant cloud consumers administrative access to virtualized IT resources (such as virtual servers), there is an inherent risk that cloud consumers could abuse this access to attack the underlying physical IT resources.
A virtualization attack exploits vulnerabilities in the virtualization platform to jeopardize its confidentiality, integrity, and/or availability.
This threat is illustrated in Figure 6.13, where a trusted attacker successfully accesses a virtual server to compromise its underlying physical server.
With public clouds, where a single physical IT resource may be providing virtualized IT resources to multiple cloud consumers, such an attack can have significant repercussions.
Figure 6.13. An authorized cloud service consumer carries out a virtualization attack by abusing its administrative access to a virtual server to exploit the underlying hardware.
If physical IT resources within a cloud are shared by different cloud service consumers, these cloud service consumers have overlapping trust boundaries.
Malicious cloud service consumers can target shared IT resources with the intention of compromising cloud consumers or other IT resources that share the same trust boundary.
The consequence is that some or all of the other cloud service consumers could be impacted by the attack and/or the attacker could use virtual IT resources against others that happen to also share the same trust boundary.
Figure 6.14. Cloud Service Consumer A is trusted by the cloud and therefore gains access to a virtual server, which it then attacks with the intention of attacking the underlying physical server and the virtual server used by Cloud Service Consumer B.
Cloud computing concept Book Link
CLOUDCOMPUTING THEORY PLAYLIST
CLOUD COMPUTING PRACTICAL PLAYLIST
Subscribe the Channel Link
IF any #Query or #Doubt #DM on #Instagram :- #bansode_ajay_2102
#bansode_tech_solution










Comments
Post a Comment